Disable any browser extensions that may be interfering with the web site. This consists of Ad blockers, privateness extensions, or VPNs which will modify World-wide-web visitors.In today's digital age, the phrase "hacker" usually conjures visuals of shadowy figures powering screens, orchestrating advanced cyber attacks. Nevertheless, not all hacker
A Secret Weapon For hire a hacker
With this tutorial We're going to discuss the thought of Ports and how they perform with IP addresses. When you've got not read our post on IP addresses and want a brush up, you could find the article listed here. For those who understand the ideas of IP addresses, then allows move ahead to TCP and UDP ports And the way they operate.Hackers who off
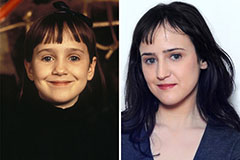 Mara Wilson Then & Now!
Mara Wilson Then & Now! Joseph Mazzello Then & Now!
Joseph Mazzello Then & Now! Ross Bagley Then & Now!
Ross Bagley Then & Now! Bug Hall Then & Now!
Bug Hall Then & Now! Andrea Barber Then & Now!
Andrea Barber Then & Now!